The Maginot Line, built by the French after World War One, is a perfect metaphor for most cybersecurity programs, particularly those of financial advisors.
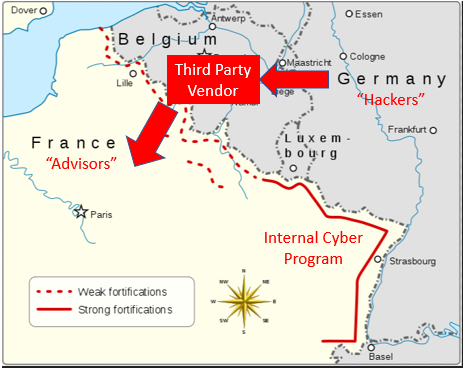
The Maginot Line: A perfect metaphor for most cybersecurity programs today.
Built by the French in the 1930s , the Maginot Line was one of the most heavily fortified borders on earth. Spanning the entire border between France and Germany, the French constructed a border system replete with rail artillery, flood zones, underground bunkers and over 5,000 watch posts. The hypothesis was simple: develop a system so robust and menacing as to discourage any direct aggression from ze Germans.
Sadly, the Maginot failed to blunt the German advance. With Belgium in plain sight, Germany sidestepped the Maginot line, pushed due West towards Brussels, and marched south towards Paris. Belgium fell in eighteen days, and the rest, as they say, is history. Some historians argue that the Maginot Line was a tremendous tactical blunder on the part of the French. Others claim the line was strategically placed to avoid a direct invasion. Better to slow the advance through Belgium, they argue. Regardless of your point of view, the impact was the same: the enemy avoided the fortified areas and attacked the weakest vulnerability.
Third Party Vendors: The Achilles’ Heel of most cybersecurity programs
And so it is with cybersecurity. Today’s focus on cyber has brought about significant improvements to the advisory landscape. Custodians, falling under stringent cyber requirements, have improved by leaps and bounds. Software and hardware are now set by default to heightened cyber standards. For example, Microsoft Windows now comes equipped with in-house encryption (BitLocker), anti-malware (Defender), and a host of other tools readily available that can harden your advisory against attack. In short, most advisors can build their own Maginot line of cybersecurity relatively quickly around what they directly control.
Where things get tricky is the use of third-party vendors. Third-party vendors, if not selected properly, can potentially be the soft underbelly of your cybersecurity landscape. A vendor with weak cyber controls is a lucrative target for cybercriminals (and one only needs to look at the Home Depot, Target, and Best Buy breaches for case studies). Think about the numerous financial planning software firms that capture a client’s entire financial landscape. Consider the third party data aggregators that collect client holdings in a central location. What about your cloud storage service or third party website/blog service? The list goes on.
Hackers, like most humans, are generally lazy. It doesn’t make sense to expend a lot of effort attacking a single advisor, with minimal data, that is relatively well prepared (encrypted hard drives, malware on, etc.). Similarly, it will be extremely difficult to crack into a custodian with a fully staffed cyber division and squirrel away funds. What is worrisome is the middle zone of players I mentioned earlier.
The SEC finds it worrisome as well:
We will continue to prioritize cybersecurity in each of our examination programs. Our examinations have and will continue to focus on, among other things, governance and risk assessment, access rights and controls, data loss prevention, vendor management, training and incident response. –SEC Office of Compliance Inspections and Examinations, 2018 (emphasis added)
Not convinced?
Check out the National Institute of Standards and Technology (NIST) framework for cybersecurity update released in April, 2018. Specifically, look at the markup version and see what they added for 2018 vis-a-vis vendor management. Below is a screenshot. Red = new addition.
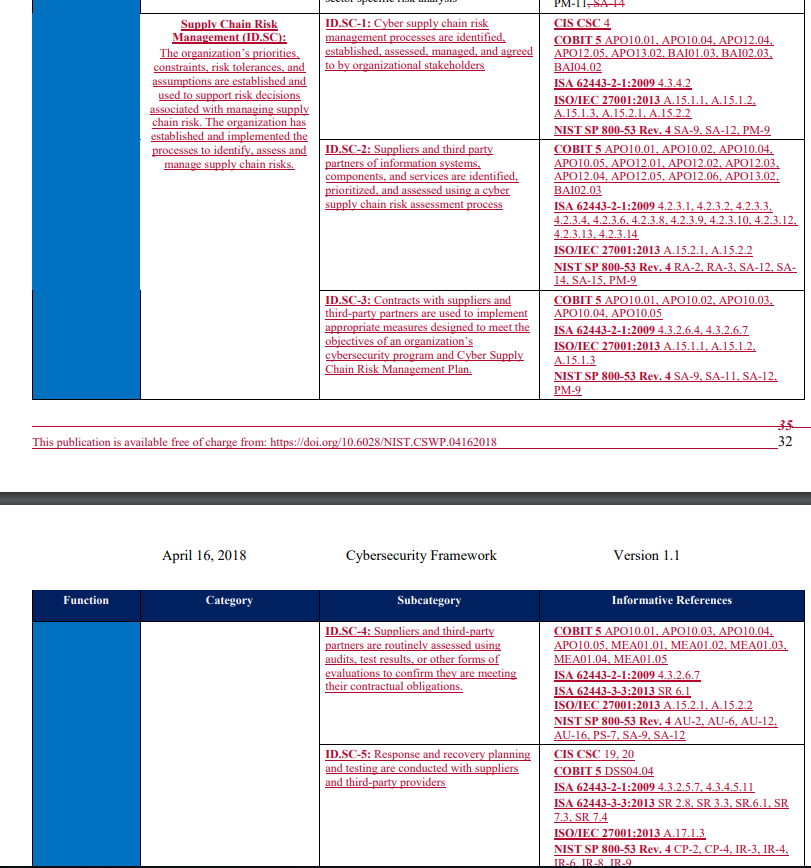
NIST added an entirely new section on vendor management. Enjoy
Yup – NIST basically added an entire section on vendor management. Whatever NIST incorporates in their 2018 framework, you can be assured it will be on the SEC’s checklist in 2019. Don’t know what NIST is? You should. Read this post and come back. Short answer: NIST sets the standards that most regulatory agencies, of all stripes, look toward when writing their compliance manuals. If your advisor follows NIST guidelines, you are more than likely good to go for any examination / regulatory inquiry.
Thanks for scaring us…but what can advisors actually do vis-a-vis vendor management???
Don’t let the new requirements intimidate you. You too can deploy a robust vendor management program.
Vendor Management really boils down to three key elements:
- Identify and triage
- Due diligence
- Monitor and test
Step 1: Identify and triage your vendors in terms of risk to the organization
Identify and triage is literally listing out ALL of your third party service providers and prioritizing them based on proximity to sensitive data (e.g., client details and trading signals) and importance to the Advisor’s critical assets (e.g., servers and the like). For example, if you have a cloud-based backup system like Dropbox, they would rank pretty high on both access to sensitive data AND importance to critical assets.
I hate to sound like a broken record in these cyber posts, but the FINRA’s Small Firm Cybersecurity Checklist is a great tool for vendor management. Simply fill out “Section 3” and boom, you have a great inventory, assessed by exposure level, of your vendors. Of course, I would recommend completing the entire checklist as part of an annual risk assessment process, but Section 3 is the vendor-specific section.
The Small Firm Cybersecurity Checklist – A must have for Advisors
Step 2: Conduct due diligence on vendors
Now comes the due diligence part. This phase can potentially involve a lot of cumbersome steps if you are not efficient and pragmatic. As always, I find it best to refer to the referees and figure out what they will actually be looking for. Much cheaper than paying a consultant, and typically, much clearer as well. The SEC’s 2015 Cybersecurity Examination Initiative remains, in my view, a great summary of what the SEC looks for (see page 4 of the Appendix for Vendor Management).

SEC guidance (2015) on vendor management examination topics. Boom shaka–laka
Super! Now, all we need to do is take this checklist, call Amazon, ask them for an update on their written contingency plans, and then get them to update their contract to provide clarity on data access, right?…good luck. Ladies and gentlemen, welcome to the wonderful intersection of regulatory intent and reality. In reality, most vendors are really big (Google), already have their standards in place, and could give two flips about you or your rinky-dink due advisory firm (rinky-dink = $100Bn in AUM and below). On the other end of the spectrum, you have “start-up” type vendors that are building the plane as they fly it and are likely grateful to have you as a customer. Probably more responsive to your requests…and probably less prepared. And finally, you have every other vendor in between Google and Chuck’s Startup Shack. Specifically, mid-tier firms that may or may not be responsive to your due diligence inquiries.
Start your due diligence process by sorting your vendors into three buckets: Big fish, medium fish, and little fish. Size of the vendor is roughly correlated with “do they care about / will they respond to my due diligence request.” For example, Google, Amazon, and Microsoft are all vendors, and (I assume) none of them will return your phone calls…sorry. Thus, they are big fish. A medium fish is most likely a mid-tier, but a sizeable player that may or may not be responsive. Finally, a small fish is a startup vendor that you can likely lean on to be responsive in due diligence. Each “bucket” of fish will require a different approach.
Let’s get started with the big fish. And to do so, I would like to introduce you to your newest best friend – the FedRamp program. A little primer on FedRamp:
Once upon a time, long long ago, back in 2003 to be exact, the President of the United States (Dubya) signed the National Strategy to Secure Cyberspace that basically said: “Hey – cybersecurity is really important. All federal agencies should do something about it. Homeland Security will take the lead, but you all need to shape up.” The agencies all scurried about implementing their own cybersecurity initiatives, to include, you guessed it, vendor management. The road to hell is paved with good intentions and federal agencies are no exception. Every federal agency started putting together their standards and guidelines for cyber. The Department of Interior had their encryption standards. NASA had a different set. And so on.
Thus, in true government fashion, a critical strategic initiative quickly blossomed into a full-blown, as we say in the Marine Corps, Charlie Foxtrot. A subsequent project was later launched in 2011 that said: “Whoa whoa whoa gang…love the initiative, but we now have twenty different standards across twenty different agencies. Let’s standardize this goat rodeo immediately.” FedRAMP was born.
Below is a graphic that illustrates how FedRamp “sits” within the federal government:

FedRAMP’s stakeholder map. Note presence of NIST
FedRamp is the one stop shop for any government agency looking to select a vendor for a variety of services (e.g., cloud storage or web hosting). Getting FedRamp certified is extremely difficult and requires ongoing recertification and testing. The positive? Any vendor in the FedRamp marketplace is generally “green light” approved for any agency to use. If it’s good enough for the NSA, chances are it’s good enough for you.
“any cloud services that hold federal data must be FedRAMP authorized” FedRAMP homepage
So…the moral of the story is: GET AS MANY VENDORS AS YOU CAN FROM FEDRAMP. Of course, Uncle Sam doesn’t give two flips about financial planning software or other advisor-centric vendors, but Google Suite, Amazon Web Services, and a host of others are either FedRamp certified currently or are in the process of getting FedRamp certified. FedRamp has the negotiating leverage, technical know-how, and resources to give anyone wanting to work with Uncle Sam a thorough proctology exam.
FedRamp certification process…in the simplest of terms.
For these large vendors, here is what you need to do:
- Confirm vendors are FedRamp certified on the FedRAMP marketplace
- Download, from their homepage, whatever white paper they may have on cybersecurity (most large firms have one)
- Document your completion of #1 and #2.
Congrats, your big fish are now “done.” FedRAMP vendors have relatively robust cyber programs that are “certified” for widespread adoption by US government agencies. Of course, no vendor is failsafe, but in terms of urgency, you can confidently place these vendors in a lower priority status.
Now. let’s turn to the smaller vendors (little fish).
Smaller vendors conceivably need you more than you need them. They may also welcome a due diligence request as it can enable greater understanding of industry requirements and the like. This category of fish is also relatively straightforward. While there is no standard approach, here is a typical approach to due diligence requests with small vendors:
Me: “Hi, as part of the SEC’s Cybersecurity Initiative, we are asking all vendors to complete this small firm checklist (send them FINRA’s) and certify their adherence to a robust cybersecurity program.”
Provider: “Uhm…and if I don’t?”
Me: “No problem! Just turn off our service effective immediately.”
Provider: “We would love to support you in this due diligence effort as cybersecurity is our top priority!”
Clearly, this conversation never happened… but variations of it have. Firms are hesitant to disclose their processes and procedures, especially when they are half-baked, or worse, non-existent. Also, it can be a tremendous burden to individually respond to a swarm of independent due diligence requests. As for what to ask, I find FINRA’s small firm checklist to be relatively robust, but you have to use common sense as well and not just rely on the checklist. Specifically, you want to be assured that the proper controls and procedures are in place to secure your data. Do all employees have access to data or are appropriate firewalls in place? Does the firm have a cybersecurity policy, cyber insurance, etc.? And don’t forget: if you didn’t document it, it didn’t happen. Ensure you are documenting your findings and storing them for future review.
Saving the worst for last: Mid-tier vendors that may or may not be responsive.
In an ideal world, all vendors are going to embrace your requests for cybersecurity. A stronger community makes all of us better, and more widespread “cyber hygiene” should be a top priority for all businesses. Nevertheless, not everyone will view the world this way and consider your diligence efforts a downright nuisance. Generally, I find these firms big enough not to worry about losing individual customers, but small enough to have never been thoroughly researched before.
Here is the chain of events that I recommend for these ‘mid-tier” vendors:
- Determine if you can seamlessly swap out this vendor for a FedRamp approved vendor (big fish)
- Determine if the supplier will provide bespoke responses to the small firm checklist (small fish)
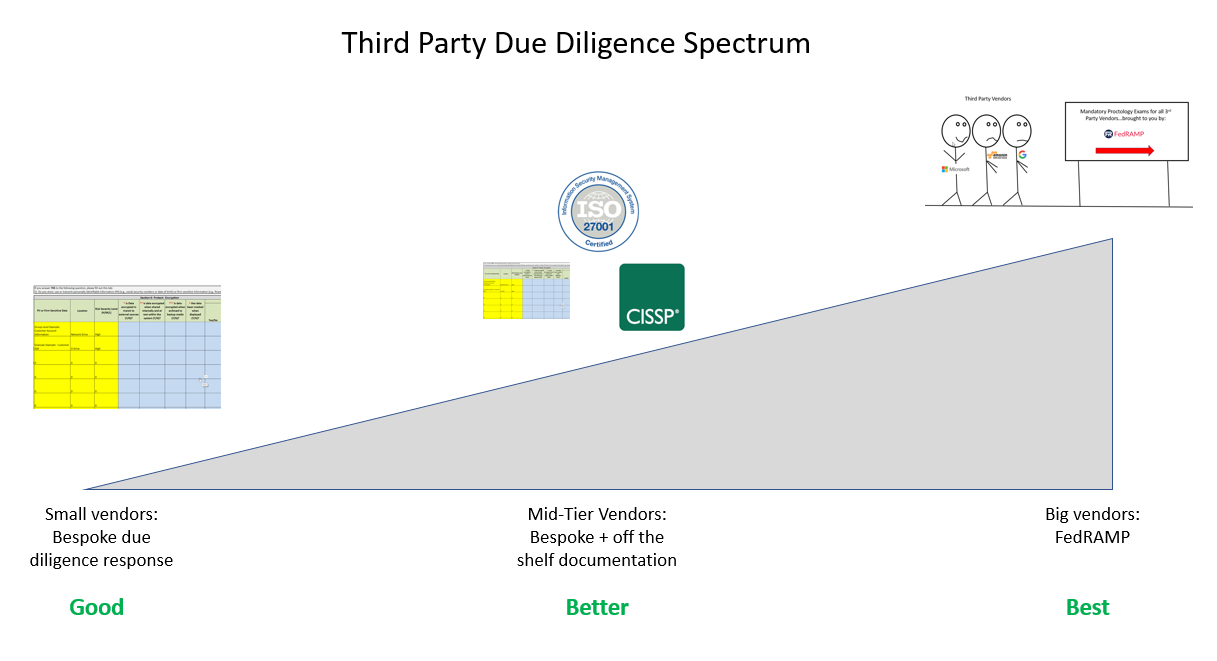
- Determine what off the shelf white papers on cybersecurity the firm publishes. Explore what certifications they have (ISO? SOC II certified? Are any staff members CISSP certified? etc.). Download and document these items wherever possible.
- Fire the vendor or modify relationship if none of the above are possible.
Where you land on this spectrum of activity is really dependent upon how critical this vendor is to your business and how willing they are to support your efforts. For certain vendors, really going through the motions and doing the heavy lifting on research and the like could be worth it if they are a mission-critical partner. Others, not so much. If you do have to go option 3, be sure to reference your research against the NIST standards and the small firm checklist. Great, free resources that will identify several considerations.
And ultimately, don’t let a stubborn vendor put your client’s data at risk. If they aren’t willing to work with you on cyber, it’s time to find someone who will. Below is a professional graphic artist rendering of the framework described:
Conclusion: Vendor management is somewhat of a pain, but it is certainly doable.
Vendor management is not going away. In fact, I would envision SEC examinations to be primarily cybersecurity examinations in the years ahead, with vendors smack dab in the middle of any audit. Nevertheless, Advisors can (and should) control their destiny here. Let’s recap the key takeaways:
- Triage your vendors and understand what approach is needed for each. Vendor management is not one-size fits all.
- Leverage FedRamp whenever possible. Uncle Sam has done the heavy lifting here.
- Use off the shelf tools to bolster your due diligence efforts (FINRA checklist, NIST framework, etc)
- Document your steps and monitor on an ongoing basis.
No approach is error-free and this post is certainly no exception. Nevertheless, compared to the ostrich head in the sand tactics that many advisors seem to be taking currently, this method can help get your vendor management efforts on the right track.
And always remember, the Compliance Officer is always watching!
About the Author: Pat Cleary
—
Important Disclosures
For informational and educational purposes only and should not be construed as specific investment, accounting, legal, or tax advice. Certain information is deemed to be reliable, but its accuracy and completeness cannot be guaranteed. Third party information may become outdated or otherwise superseded without notice. Neither the Securities and Exchange Commission (SEC) nor any other federal or state agency has approved, determined the accuracy, or confirmed the adequacy of this article.
The views and opinions expressed herein are those of the author and do not necessarily reflect the views of Alpha Architect, its affiliates or its employees. Our full disclosures are available here. Definitions of common statistics used in our analysis are available here (towards the bottom).
Join thousands of other readers and subscribe to our blog.